Job Opening: Debian Linux System Administrator at Kumina
 March 11th, 2016
March 11th, 2016
We’re growing and are looking for Debian Linux System Administors that would like to grow with us and provide sysadmin services to our customers. TL;DR: (in random order) Debian Linux / Apache / PHP / MySQL / Python / Puppet / KVM / Qemu / PostgreSQL / Tomcat / GlassFish / Logstash / ElasticSearch / […]
More... February 11th, 2014
February 11th, 2014
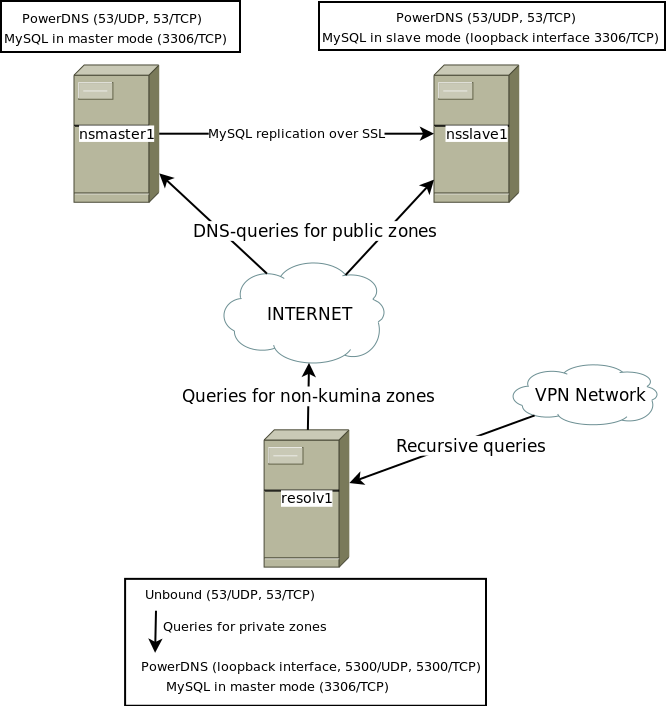 August 15th, 2013
August 15th, 2013
 December 9th, 2011
December 9th, 2011
 June 17th, 2011
June 17th, 2011