On our new DNS infrastructure (and DNSSEC)
 August 15th, 2013
August 15th, 2013
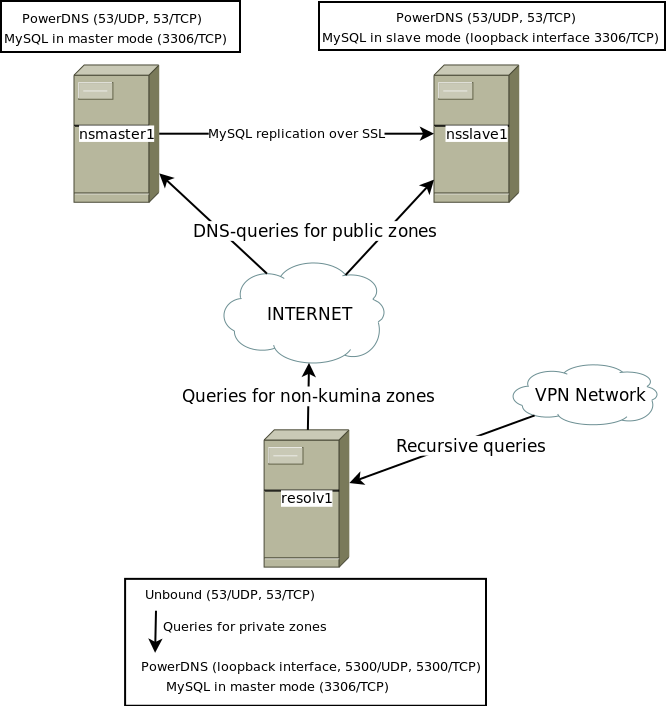
Recently we’ve been busy implementing a new DNS infrastructure for our resolvers as well as our authoritative servers. We wanted to be ready for future developments like DNSSEC and we wanted to re-new this important part of our infrastructure for a while. This blog-post gives an overview of our new setup.
More... April 29th, 2011
April 29th, 2011